Exposed files leak details on SORM
... Russia's pervasive domestic surveillance system
A California-based security company on Thursday revealed its researchers had discovered more than 1.7 terabytes of proprietary telecommunications data left publicly online, including hardware specifications for a lawful surveillance device used throughout the Russian Federation.
TechCrunch first reported on the exposed files discovered by a data breach hunter working at UpGuard.
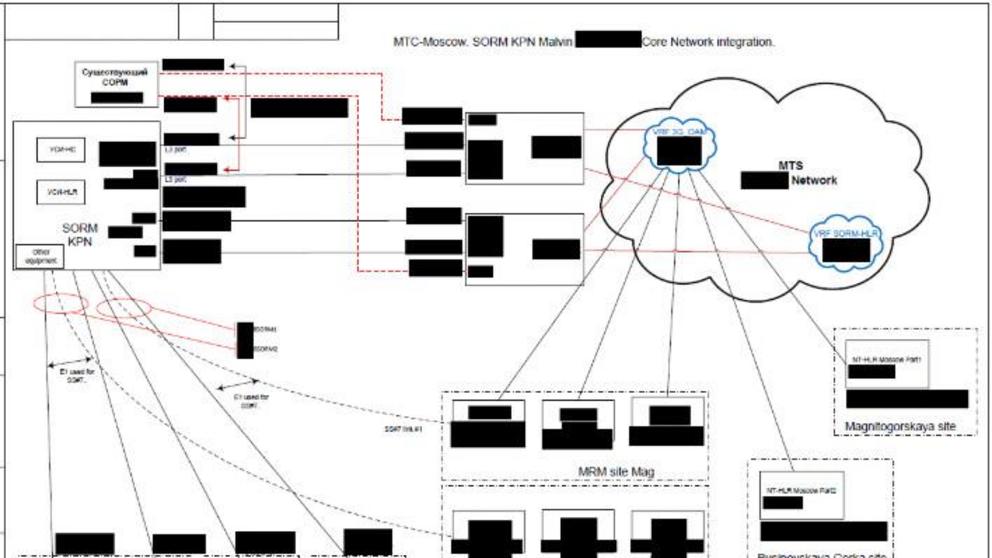
Among the cache are reportedly documents detailing a major infrastructure project involving the installation of lawful intercept devices used by Russian authorities to surreptitiously collect phone and internet communications. The documents appear to primarily concern Mobile TeleSystems (MTS), Russia’s largest telecom company, and Nokia, which maintains and updates MTS’s network.
The devices — known in the West as “SORM” or “System for Operative Investigative Activities” — are a key facet of Russian domestic surveillance. Approved for use by the FSB, Russia’s federal security service (formerly known as the KGB), Russian law mandates that telecom operators install and maintain the devices, the first of which was developed in 1995. The latest version of SORM, which was rolled out in 2014, reportedly also performs deep packet inspection.
Other Russian agencies may also tap into the data collected by SORM, including the SBP, President Vladimir Putin’s personal security service. Work related to SORM is typically classified, an expert at Russian digital-rights told TechCrunch.
Dozens of countries require telecom providers to retain certain data and install technologies for real-time eavesdropping. Privacy protections range from strong in some countries to others where rules restricting police access are non-existent.
With passage of the Yarovaya law in 2016, Russian telecoms are required to store text messages, phone conversations, and other communications for up to six months. Metadata, likewise, for up to three years. Authorities do not require a court order to access it.
In the U.S., a warrant issued on probable cause is generally required before law enforcement can access the same kinds of information, in all but a few circumstances.
Certain “national security” exemptions do exist enabling agencies, such as the FBI, to collect some internet and phone data without a warrant. Emails stored remotely for 181 days or more may also be obtained warrantlessly under the Stored Communications Act, as another example.
An exposed document showing Nokia’s involvement in installing SORM devices. (Screenshot: UpGuard)
UpGuard reports that the exposed data was stored on an unprotected backup device and that it appeared to belong mostly to Nokia, which later confirmed that a Nokia employee handed the data over to an unnamed third party who “failed to follow his company’s business processes, security policies, and his personal responsibility to protect it,” according to UpGuard.
UpGuard reported that the data was no longer publicly accessible as of September 14.
“Exposing any data related to a system with the power and secrecy of SORM to the public internet is an event,” UpGuard said in a statement. “Leaking what appears to be an inventory of the most recent generation of installed hardware for a nation’s largest telecom provider is unprecedented.”
Read the full UpGuard report here.
For the rest of this article please go to source link below.